In this post I will do an installation on DVWA in Kali Linux using the step from the slides given in binusmaya.
The first step is to change directory in the terminal into /var/www/html and then download the file through the link by using the command wget https://github.com/ethicalhack3r/DVWA/archive/master.zip after finished with the download then unzip the file using unzip master.zip command after that confirming that the file really exist at the file location by using ls command.
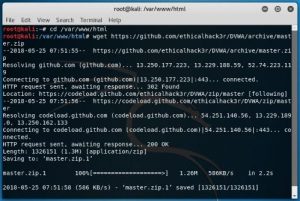
Above is the process I do from changing the directory and downloading the DVWA file.
Below is the process of unziping the master.zip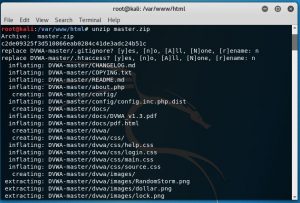
because i lost the screen capture of this process i redo the process and recapture but the terminal indicate that i have a same file and asking to replace it or not.
Below is to check if the file exist at the folder location.
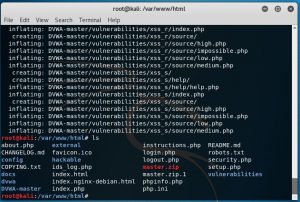
It can be seen in the directory of var/www/html that the master.zip really did exist.
The next step is to move the content from directory DVWA-Master to web root directory by using “mv DVWA-Master/* /var/www/html” command then changing the owner directory of var/www/html by using “chown -R www-data:www-data /var/www/html” as shown below.
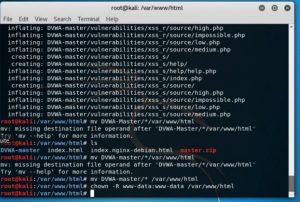
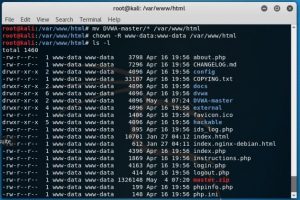
After that the tutorial shows the directory with details using ls -la command.
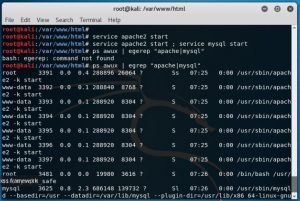
After that starting the service of apache2 and mysql by using “service apache2 start; service mysql start” as seen below
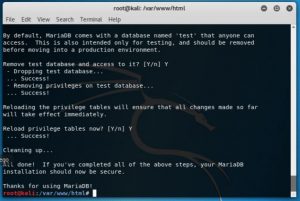
After that following the instruction next step is to secure mysql installation by using “mysql secure installation” command then you will be asked whether you want to change password or not. In the tutorial the user change the password so i also did the same.
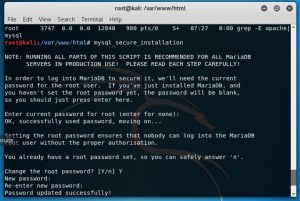
After changing the password I got some question from the system like “Remove anonymous users?”, “Disallow root login remotely?”, “Remove test database and access to it?”, “Reload privilege tables now?” and the answer to all that is yes. It is done to prevent others from accessing the mysql of the system.

After following the next step it is quite strange that I didn’t find any error that are mentioned in the slides but I still follow the following command after the supposed to be error step to config the not available error. The command for the config is “cp config/config.inc.php.dist config/config.inc.php”.
As seen above there are no error in going to the ip of kali.
Since I didn’t find the error I’m stuck at the recaptcha step so i jumped to the setting up the database by using mysql -u root -p command after that command the system will ask for the password. but in my case the system didn’t ask the password so it directly goes into the database configuration as seen below.
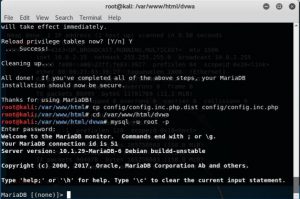
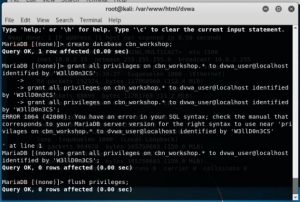
after that following the command given in the slide “create database cbn_workshop;” to create the database after that granting all privilege with a password of W3llD0n3CS by using “grant all privileges on cbn_workshop.* to dvwa_user@localhost identified by ‘W3llD0n3CS’ ” command as seen below. Other than that the tutorial have another command to flush all other privilege other than dvwa_user.
but after asking help from Mr Charles he said that the website need to have /index.php on the behind of the ip.
As seen above it brings me to the DVWA login site.
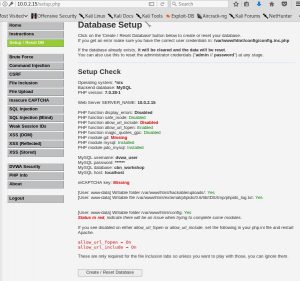
I don’t know the username and password until the class with Mr Kalpin that he told us that the username is admin and the password is password. After logging in the site brings me to the database setup page.